Device driver
| Operating systems |
|---|
 |
| Common features |
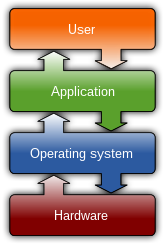
In the context of an operating system, a device driver is a computer program that operates or controls a particular type of device that is attached to a computer or automaton.[1] A driver provides a software interface to hardware devices, enabling operating systems and other computer programs to access hardware functions without needing to know precise details about the hardware being used.
A driver communicates with the device through the computer bus or communications subsystem to which the hardware connects. When a calling program invokes a routine in the driver, the driver issues commands to the device (drives it). Once the device sends data back to the driver, the driver may invoke routines in the original calling program.
Drivers are hardware dependent and operating-system-specific. They usually provide the interrupt handling required for any necessary asynchronous time-dependent hardware interface.[2]
Purpose
[edit]The main purpose of device drivers is to provide abstraction by acting as a translator between a hardware device and the applications or operating systems that use it.[1] Programmers can write higher-level application code independently of whatever specific hardware the end-user is using. For example, a high-level application for interacting with a serial port may simply have two functions for "send data" and "receive data". At a lower level, a device driver implementing these functions would communicate to the particular serial port controller installed on a user's computer. The commands needed to control a 16550 UART are much different from the commands needed to control an FTDI serial port converter, but each hardware-specific device driver abstracts these details into the same (or similar) software interface.
Development
[edit]Writing a device driver requires an in-depth understanding of how the hardware and the software works for a given platform function. Because drivers require low-level access to hardware functions in order to operate, drivers typically operate in a highly privileged environment and can cause system operational issues if something goes wrong. In contrast, most user-level software on modern operating systems can be stopped without greatly affecting the rest of the system. Even drivers executing in user mode can crash a system if the device is erroneously programmed. These factors make it more difficult and dangerous to diagnose problems.[3]
The task of writing drivers thus usually falls to software engineers or computer engineers who work for hardware-development companies. This is because they have better information than most outsiders about the design of their hardware. Moreover, it was traditionally considered in the hardware manufacturer's interest to guarantee that their clients can use their hardware in an optimum way. Typically, the Logical Device Driver (LDD) is written by the operating system vendor, while the Physical Device Driver (PDD) is implemented by the device vendor. However, in recent years, non-vendors have written numerous device drivers for proprietary devices, mainly for use with free and open source operating systems. In such cases, it is important that the hardware manufacturer provide information on how the device communicates. Although this information can instead be learned by reverse engineering, this is much more difficult with hardware than it is with software.
Microsoft has attempted to reduce system instability due to poorly written device drivers by creating a new framework for driver development, called Windows Driver Frameworks (WDF). This includes User-Mode Driver Framework (UMDF) that encourages development of certain types of drivers—primarily those that implement a message-based protocol for communicating with their devices—as user-mode drivers. If such drivers malfunction, they do not cause system instability. The Kernel-Mode Driver Framework (KMDF) model continues to allow development of kernel-mode device drivers, but attempts to provide standard implementations of functions that are known to cause problems, including cancellation of I/O operations, power management, and plug and play device support.
Apple has an open-source framework for developing drivers on macOS, called I/O Kit.
In Linux environments, programmers can build device drivers as parts of the kernel, separately as loadable modules, or as user-mode drivers (for certain types of devices where kernel interfaces exist, such as for USB devices). Makedev includes a list of the devices in Linux, including ttyS (terminal), lp (parallel port), hd (disk), loop, and sound (these include mixer, sequencer, dsp, and audio).[4]
Microsoft Windows .sys files and Linux .ko files can contain loadable device drivers. The advantage of loadable device drivers is that they can be loaded only when necessary and then unloaded, thus saving kernel memory.
Privilege levels
[edit]Depending on the operating system, device drivers may be permitted to run at various different privilege levels. The choice of which level of privilege the drivers are in is largely decided by the type of kernel an operating system uses. An operating system which uses a monolithic kernel, such as the Linux kernel, will typically run device drivers with the same privilege as all other kernel objects. By contrast, a system designed around microkernel, such as Minix, will place drivers as processes independent from the kernel but that use it for essential input-output functionalities and to pass messages between user programs and each other.[5] On Windows NT, a system with a hybrid kernel, it is common for device drivers to run in either kernel-mode or user-mode.[6]
The most common mechanism for segregating memory into various privilege levels is via protection rings. On many systems, such as those with x86 and ARM processors, switching between rings imposes a performance penalty, a factor that operating system developers and embedded software engineers consider when creating drivers for devices which are preferred to be run with low latency, such as network interface cards. The primary benefit of running a driver in user mode is improved stability, since a poorly written user-mode device driver cannot crash the system by overwriting kernel memory.[7]
Applications
[edit]Because of the diversity of modern[update] hardware and operating systems, drivers operate in many different environments.[8] Drivers may interface with:
- Printers
- Video adapters
- Network cards
- Sound cards
- PC chipsets
- Local buses of various sorts—in particular, for bus mastering on modern systems
- Low-bandwidth I/O buses of various sorts (for pointing devices such as mice, keyboards, etc.)
- Computer storage devices such as hard disk, CD-ROM, and floppy disk buses (ATA, SATA, SCSI, SAS)
- Implementing support for different file systems
- Image scanners
- Digital cameras
- Digital terrestrial television tuners
- Radio frequency communication transceiver adapters for wireless personal area networks as used for short-distance and low-rate wireless communication in home automation, (such as example Bluetooth Low Energy (BLE), Thread, Zigbee, and Z-Wave).
- IrDA adapters
Common levels of abstraction for device drivers include:
- For hardware:
- Interfacing directly
- Writing to or reading from a device control register
- Using some higher-level interface (e.g. Video BIOS)
- Using another lower-level device driver (e.g. file system drivers using disk drivers)
- Simulating work with hardware, while doing something entirely different[9]
- For software:
- Allowing the operating system direct access to hardware resources
- Implementing only primitives
- Implementing an interface for non-driver software (e.g. TWAIN)
- Implementing a language, sometimes quite high-level (e.g. PostScript)
So choosing and installing the correct device drivers for given hardware is often a key component of computer system configuration.[10]
Virtual device drivers
[edit]Virtual device drivers represent a particular variant of device drivers. They are used to emulate a hardware device, particularly in virtualization environments, for example when a DOS program is run on a Microsoft Windows computer or when a guest operating system is run on, for example, a Xen host. Instead of enabling the guest operating system to dialog with hardware, virtual device drivers take the opposite role and emulates a piece of hardware, so that the guest operating system and its drivers running inside a virtual machine can have the illusion of accessing real hardware. Attempts by the guest operating system to access the hardware are routed to the virtual device driver in the host operating system as e.g., function calls. The virtual device driver can also send simulated processor-level events like interrupts into the virtual machine.
Virtual devices may also operate in a non-virtualized environment. For example, a virtual network adapter is used with a virtual private network, while a virtual disk device is used with iSCSI. A good example for virtual device drivers can be Daemon Tools.
There are several variants of virtual device drivers, such as VxDs, VLMs, and VDDs.
Open source drivers
[edit]- Graphics device driver
- Printers: CUPS
- RAIDs: CCISS[11] (Compaq Command Interface for SCSI-3 Support[12])
- Scanners: SANE
- Video: Vidix, Direct Rendering Infrastructure
Solaris descriptions of commonly used device drivers:
- fas: Fast/wide SCSI controller
- hme: Fast (10/100 Mbit/s) Ethernet
- isp: Differential SCSI controllers and the SunSwift card
- glm: (Gigabaud Link Module[13]) UltraSCSI controllers
- scsi: Small Computer Serial Interface (SCSI) devices
- sf: soc+ or social Fiber Channel Arbitrated Loop (FCAL)
- soc: SPARC Storage Array (SSA) controllers and the control device
- social: Serial optical controllers for FCAL (soc+)
APIs
[edit]- Windows Display Driver Model (WDDM) – the graphic display driver architecture for Windows Vista and later.
- Unified Audio Model (UAM)[14]
- Windows Driver Foundation (WDF)
- Declarative Componentized Hardware (DCH) - Universal Windows Platform driver[15]
- Windows Driver Model (WDM)
- Network Driver Interface Specification (NDIS) – a standard network card driver API
- Advanced Linux Sound Architecture (ALSA) – the standard Linux sound-driver interface
- Scanner Access Now Easy (SANE) – a public-domain interface to raster-image scanner-hardware
- Installable File System (IFS) – a filesystem API for IBM OS/2 and Microsoft Windows NT
- Open Data-Link Interface (ODI) – network card API similar to NDIS
- Uniform Driver Interface (UDI) – a cross-platform driver interface project
- Dynax Driver Framework (dxd) – C++ open source cross-platform driver framework for KMDF and IOKit[16]
Identifiers
[edit]A device on the PCI bus or USB is identified by two IDs which consist of two bytes each. The vendor ID identifies the vendor of the device. The device ID identifies a specific device from that manufacturer/vendor.
A PCI device has often an ID pair for the main chip of the device, and also a subsystem ID pair which identifies the vendor, which may be different from the chip manufacturer.
Security
[edit]Devices often have a large number of diverse and customized device drivers running in their operating system (OS) kernel and often contain various bugs and vulnerabilities, making them a target for exploits.[17] Bring Your Own Vulnerable Driver (BYOVD) uses signed, old drivers that contain flaws that allow hackers to insert malicious code into the kernel.[18]
There is a lack of effective kernel vulnerability detection tools, especially for closed-source OSes such as Microsoft Windows[19] where the source code of the device drivers is mostly not public (open source)[20] and the drivers often also have many privileges.[21][22][23][24]
Such vulnerabilities also exist in drivers in laptops,[25] drivers for WiFi and bluetooth,[26][27] gaming/graphics drivers,[28] and drivers in printers.[29]
A group of security researchers considers the lack of isolation as one of the main factors undermining kernel security,[30] and published a isolation framework to protect operating system kernels, primarily the monolithic Linux kernel which, according to them, gets ~80,000 commits/year to its drivers.[31][32]
An important consideration in the design of a kernel is the support it provides for protection from faults (fault tolerance) and from malicious behaviours (security). These two aspects are usually not clearly distinguished, and the adoption of this distinction in the kernel design leads to the rejection of a hierarchical structure for protection.[33]
The mechanisms or policies provided by the kernel can be classified according to several criteria, including: static (enforced at compile time) or dynamic (enforced at run time); pre-emptive or post-detection; according to the protection principles they satisfy (e.g., Denning[34][35]); whether they are hardware supported or language based; whether they are more an open mechanism or a binding policy; and many more.See also
[edit]References
[edit]- ^ a b "What is all device driver?". WhatIs.com. TechTarget. Archived from the original on 13 February 2021. Retrieved 19 March 2018.
- ^ EMC Education Services (2010). Information Storage and Management: Storing, Managing, and Protecting Digital Information. John Wiley & Sons. ISBN 9780470618332. Archived from the original on 2021-02-13. Retrieved 2020-11-10.
- ^ Burke, Timothy (1995). Writing device drivers: tutorial and reference. Digital Press. ISBN 9781555581411. Archived from the original on 2021-01-26. Retrieved 2016-08-05.
- ^ "MAKEDEV — Linux Command — Unix Command". Linux.about.com. 2009-09-11. Archived from the original on 2009-04-30. Retrieved 2009-09-17.
- ^ Tanenbaum, Andrew; Woodhull, Albert (2006). Operating Systems, Design and Implementation (3rd. ed.). Upper Saddle River, NJ: Pearson Pretence Hall. p. 256. ISBN 0-13-142938-8.
- ^ Yosifovich, Pavel; Ionescu, Alex; Russinovich, Mark; Solomon, David (2017). Windows Internals, Part 1 (Seventh ed.). Redmond, Washington: Microsoft Press. ISBN 978-0-7356-8418-8.
- ^ "Introduction to the User-Mode Driver Framework (UMDF)". Microsoft. 2006-10-10. Archived from the original on 2010-01-07. Retrieved 2008-03-04.
- ^ Deborah Morley (2009). Understanding Computers 2009: Today and Tomorrow. Cengage Learning. ISBN 9780324830132. Archived from the original on 2021-06-09. Retrieved 2020-11-10.
- ^ Computer Peripherals and Interfaces. Technical Publications Pune. January 2008. pp. 5–8. ISBN 978-8184314748. Retrieved 2016-05-03.[permanent dead link]
- ^ "What are Device Drivers and why do we need them?". drivers.com. April 17, 2015. Archived from the original on November 20, 2016. Retrieved March 19, 2018.
- ^ "CCISS". SourceForge. 2010. Archived from the original on 2010-08-21. Retrieved 2010-08-11.
Drivers for the HP (previously Compaq) Smart Array controllers which provide hardware RAID capability.
- ^ Russell, Steve; et al. (2003-10-21). Abbreviations and acronyms. IBM International Technical Support Organization. p. 207. ISBN 0-7384-2684-9. Retrieved 2011-08-14.
{{cite book}}:|work=ignored (help)[permanent dead link] - ^ "US Patent 5969841 - Gigabaud link module with received power detect signal". PatentStorm LLC. Archived from the original on 2011-06-12. Retrieved 2009-09-08.
An improved Gigabaud Link Module (GLM) is provided for performing bi-directional data transfers between a host device and a serial transfer medium.
- ^ "Unified Audio Model (Windows CE 5.0)". Microsoft Developer Network. Archived from the original on 2017-06-22. Retrieved 2016-09-19.
- ^ Dell US. "What are DCH drivers and why do you need to know about them? | Dell US". www.dell.com. Retrieved 2020-10-29.
- ^ "dxd - dynax driver framework: Main Page". dxd.dynax.at. Archived from the original on 2016-05-29. Retrieved 2016-09-19.
- ^ Talebi, Seyed Mohammadjavad Seyed; Tavakoli, Hamid; Zhang, Hang; Zhang, Zheng; Sani, Ardalan Amiri; Qian, Zhiyun (2018). Charm: Facilitating Dynamic Analysis of Device Drivers of Mobile Systems. pp. 291–307. ISBN 9781939133045. Archived from the original on 5 November 2022. Retrieved 5 November 2022.
- ^ Goodin, Dan (14 October 2022). "How a Microsoft blunder opened millions of PCs to potent malware attacks". Ars Technica. Archived from the original on 8 November 2022. Retrieved 8 November 2022.
- ^ Pan, Jianfeng; Yan, Guanglu; Fan, Xiaocao (2017). Digtool: A {Virtualization-Based} Framework for Detecting Kernel Vulnerabilities. pp. 149–165. ISBN 9781931971409. Retrieved 5 November 2022.
- ^ King, Bertel (18 June 2022). "Closed Source vs. Open Source Hardware Drivers: Why It Matters". MUO. Archived from the original on 5 November 2022. Retrieved 5 November 2022.
- ^ Branscombe, Mary (7 April 2022). "How Microsoft blocks vulnerable and malicious drivers in Defender, third-party security tools and in Windows 11". TechRepublic. Archived from the original on 5 November 2022. Retrieved 5 November 2022.
- ^ Goodin, Dan (5 October 2022). "No fix in sight for mile-wide loophole plaguing a key Windows defense for years". Ars Technica. Archived from the original on 5 November 2022. Retrieved 5 November 2022.
- ^ Davenport, Corbin. ""Bring Your Own Vulnerable Driver" Attacks Are Breaking Windows". How-To Geek. Archived from the original on 5 November 2022. Retrieved 5 November 2022.
- ^ "Windows 10 Security Alert: Vulnerabilities Found in Over 40 Drivers". BleepingComputer. Archived from the original on 5 November 2022. Retrieved 5 November 2022.
- ^ Goodin, Dan (13 July 2022). "Vulnerabilities that could allow undectable infections affect 70 Lenovo laptop models". Ars Technica. Archived from the original on 5 November 2022. Retrieved 5 November 2022.
- ^ Ridley, Jacob (9 February 2022). "You're going to want to update your Wi-Fi and Bluetooth drivers today". PC Gamer. Archived from the original on 5 November 2022. Retrieved 5 November 2022.
- ^ "Wireless 'BlueBorne' Attacks Target Billions of Bluetooth Devices". threatpost.com. Archived from the original on 5 November 2022. Retrieved 5 November 2022.
- ^ Spadafora, Anthony (12 January 2022). "Installing gaming drivers might leave your PC vulnerable to cyberattacks". TechRadar. Archived from the original on 5 November 2022. Retrieved 5 November 2022.
- ^ "HP patches vulnerable driver lurking in printers for 16 years". ZDNET. Archived from the original on 5 November 2022. Retrieved 5 November 2022.
- ^ "Fine-grained kernel isolation". mars-research.github.io. Archived from the original on 15 September 2022. Retrieved 15 September 2022.
- ^ Fetzer, Mary. "Automatic device driver isolation protects against bugs in operating systems". Pennsylvania State University via techxplore.com. Archived from the original on 15 September 2022. Retrieved 15 September 2022.
- ^ Huang, Yongzhe; Narayanan, Vikram; Detweiler, David; Huang, Kaiming; Tan, Gang; Jaeger, Trent; Burtsev, Anton (2022). "KSplit: Automating Device Driver Isolation" (PDF). Archived (PDF) from the original on 15 September 2022. Retrieved 15 September 2022.
- ^ Wulf 1974 pp.337–345
- ^ Denning 1976
- ^ Swift 2005, p.29 quote: "isolation, resource control, decision verification (checking), and error recovery."
